基于msf工具复现永恒之蓝漏洞
## 靶机与攻击机准备 1. 靶机:Windows Sever 2008 R2 64位 ip:192.168.137.131 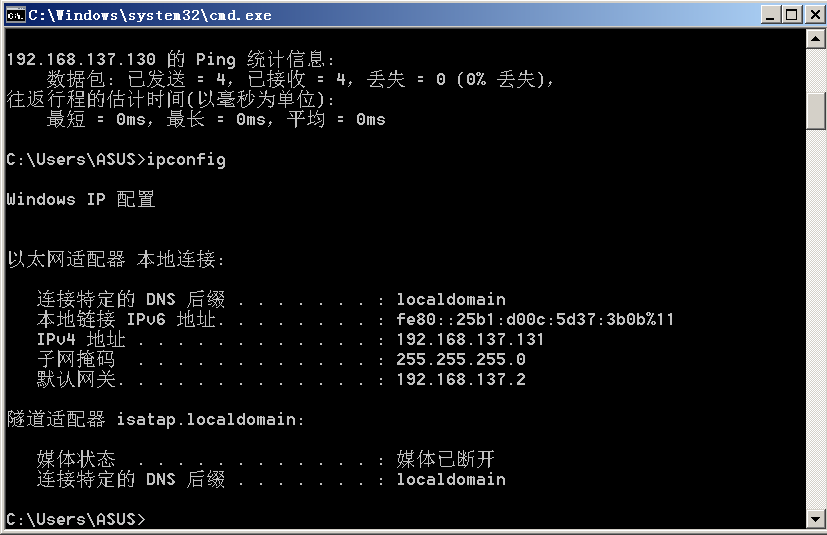 2.攻击机:Kali 2023 64位#
ctfshow web257php反序列化漏洞
最近在学php反序列化漏洞,找课外练习做的时候遇到了,觉得挺有意思,分享一下 先看下源码 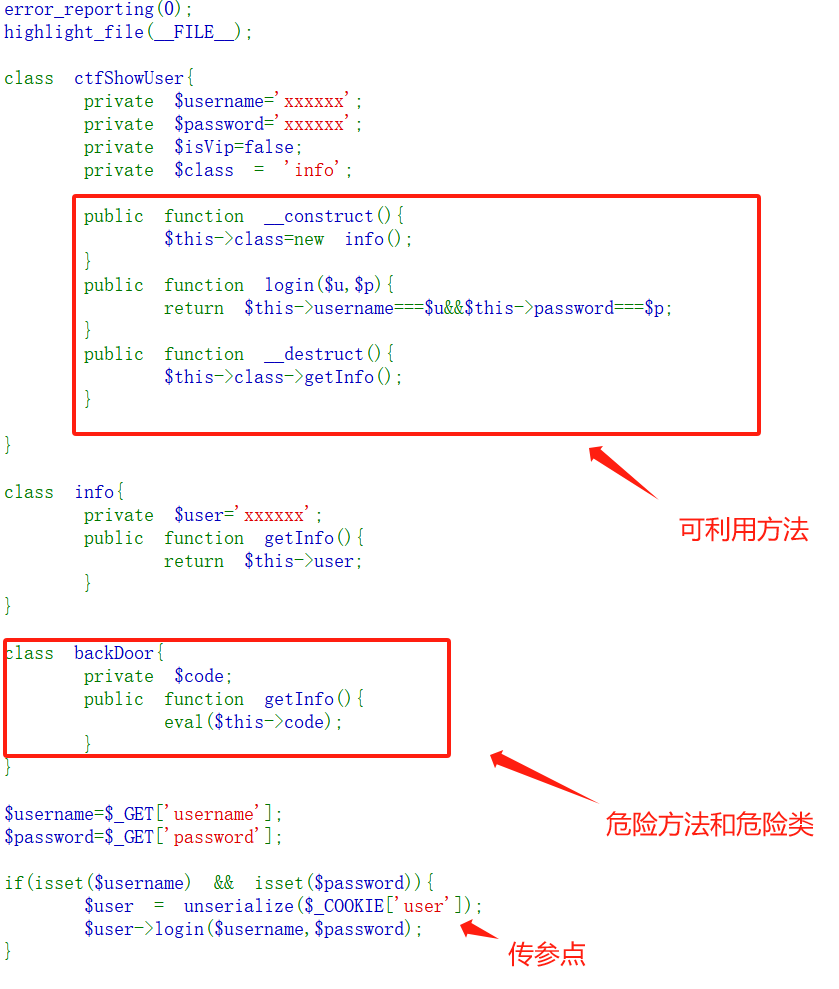 ------------ 分
1